This report, authored by Tiger Research, provides a detailed look at Bitcoin's infrastructure layer, including analysis of key projects.
TL;DR
Bitcoin as an Anchor of Trust L1: BTCFi infrastructure is built around Bitcoin's secure and conservative base layer, keeping complex logic off-chain while using Bitcoin for final settlement and verification. Concepts like BitVM can extend Bitcoin's smart contract functionality without changing consensus.
A multi-layered ecosystem for implementation: From Bitcoin-anchored blockchains like Stacks, to BTC staking chains like Botanix and Bouncebit, to rollup-based systems like Merlin and BitLayer, each approach balances scalability, programmability, and trust in a different way, while keeping Bitcoin at the center of security and value.
Complementary systems like Lightning: While Lightning excels at faster and cheaper payments than DeFi, its liquidity and routing potential have the potential to bridge Bitcoin's transaction layer with BTCFi's capital markets, opening up hybrid use cases as bridging technologies mature.
As discussed in Part 1, BTCFi aims to awaken dormant Bitcoin capital and transform it into a productive asset. However, robust infrastructure is essential for this to happen.
This section analyzes the infrastructure layers powering Bitcoin DeFi. It covers the entire spectrum, from Bitcoin's base layer to emerging Layer 2s, sidechains, and new execution environments.
These infrastructure components enable DeFi applications to be built around Bitcoin without compromising its core principles.
1. Bitcoin L1: Payments, Finality, and Trust
At the core of BTCFi lies the Bitcoin Layer 1 blockchain. It is the most secure and decentralized financial ledger in existence. It has operated virtually uninterrupted for over a decade and has a track record of careful upgrades. These characteristics make Bitcoin Layer 1 the definitive benchmark and payment method in the cryptocurrency industry.
These fundamental strengths give Bitcoin a unique role. In a multi-layered DeFi system, Bitcoin serves as the bedrock of trust. BTCFi protocols connect to Bitcoin L1 for settlement, not computation. It serves as the "highest court" that verifies transaction results.
The key point is that BTCFi doesn't touch the Bitcoin base layer to implement DeFi logic. Its mainstream design philosophy relies on Bitcoin's simplicity and immutability. Execution is handled off-chain, on Layer 2, or on a sidechain, while payments and security are always returned to Bitcoin's L1 layer.
Some experimental designs differ. Certain zk-rollup implementations may benefit from new opcodes (such as OP_CAT) that require a soft fork. However, these proposals remain speculative. Most BTCFi infrastructure focuses on increasing usability while leaving Bitcoin's core consensus rules intact.
Proposals like BitVM will further push this direction. BitVM is an early concept that allows complex programs to run off-chain while Bitcoin verifies the results. It's like solving a difficult math problem on paper and publishing the answer. If no objections are raised, the result is considered valid. If someone raises a problem, they must prove it on-chain within a set time limit, and Bitcoin confirms the result.
This would allow for the execution of full-fledged smart contracts without altering the core Bitcoin system. While still experimental, it demonstrates a broader trend: Bitcoin remains a trust-based platform, while advanced features and logic are moved to external layers.
Ultimately, Bitcoin's L1 is deliberately simple and conservative, and that's why it works. It serves as a payment layer and value anchor in a growing modular ecosystem. It's not about replacing Bitcoin with Ethereum. BTCFi aims to expand Bitcoin's utility while preserving its integrity.
The following sections cover the structure of the execution layers, their design differences, and how Bitcoin supports a wider range of financial applications.
Be the first to discover insights from the Asian Web3 market, read by over 13,000 Web3 market leaders.
2. Bitcoin Anchor Chain
Bitcoin anchor chains are independent execution environments. They secure and legitimize Bitcoin through its hashing power and on-chain transactions. They operate their own consensus algorithm, but are "anchored" in a way that allows them to benefit from Bitcoin's security without directly executing logic on Bitcoin's L1.
This is like building a residential complex next to a well-protected national reserve. The sidechain residential complex has its own roads and buildings, but utilizes the reserve's security facilities for security. While it doesn't alter the reserve itself, it benefits from its authority and security.
These anchoring methods are broadly divided into three types.
Merge Mining: A method in which Bitcoin miners verify sidechain blocks simultaneously.
Proof of Transfer (PoX): Electing a block producer using Bitcoin transactions as input.
Timestamping & Checkpointing: A method for periodically recording the state of the chain in Bitcoin.
However, these chains do not inherently guarantee trustlessness. Some require a federated trustee to manage BTC deposits and withdrawals. Others establish indirect economic or timestamp-based connections to Bitcoin.
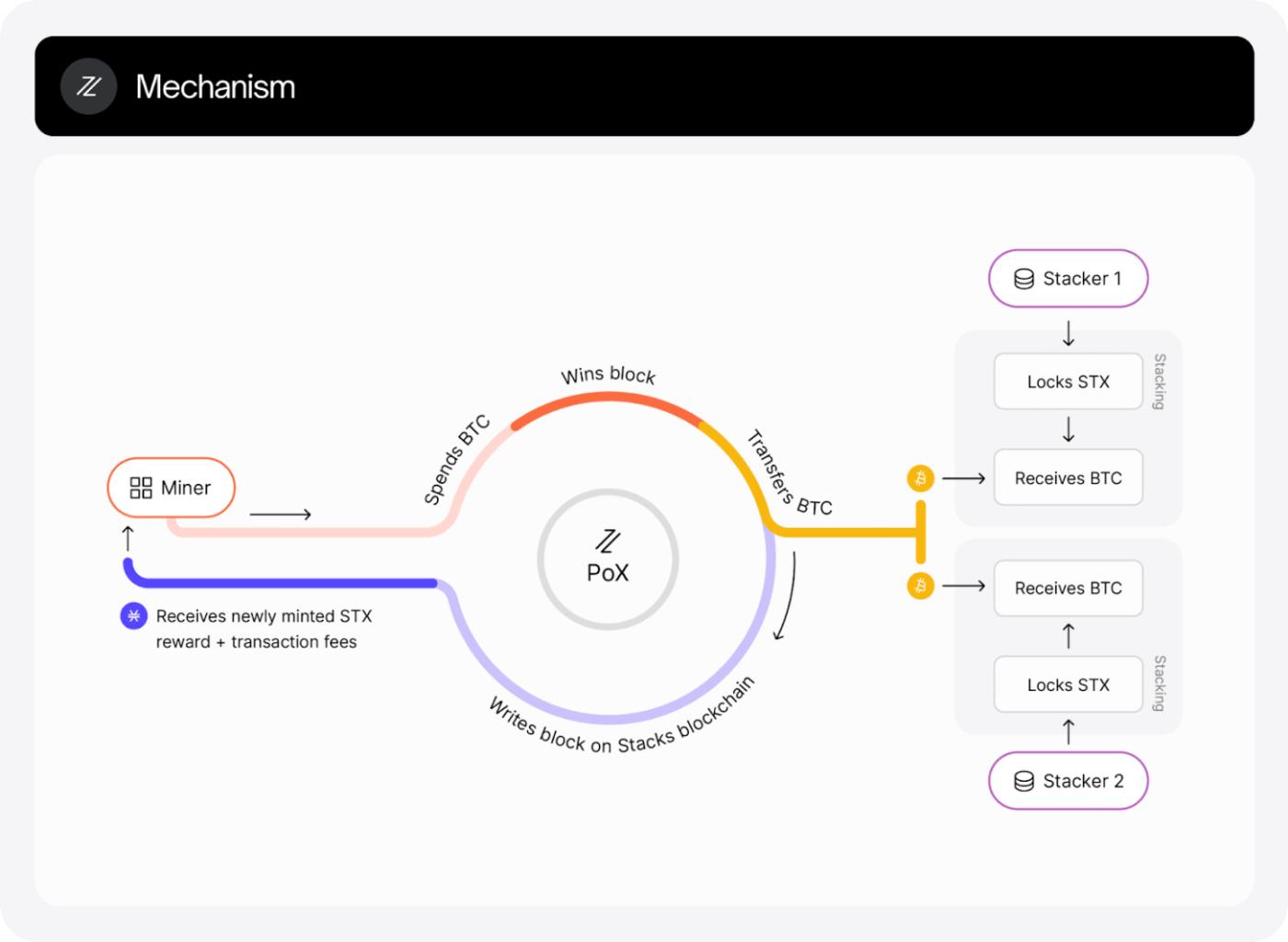
2.1. Stacks: A PoX Sidechain with Bitcoin Finality
Stacks is a prime example of a Bitcoin anchor chain that connects to Bitcoin through its own consensus mechanism called Proof of Transaction (PoX). Under PoX, Stacks miners send transactions to the Bitcoin network, spending BTC to compete for block creation rights on the Stacks chain.
This structure is linked to Bitcoin's economic system by utilizing Bitcoin's economic value itself in the consensus mechanism.
Stacks anchors its state to Bitcoin at this point. Each time a Stacks block is created, a special transaction records the information in Bitcoin, leaving the Stacks block hash on Bitcoin. This ensures the chain history receives proof of date and is tamper-proof.
3. BTC staking or hybrid PoS chain
Require validators to stake BTC as collateral (usually at L1)
Fairly selecting node operators using Bitcoin block entropy (randomness of block hash).
Create a tamper-proof audit trail by anchoring checkpoints to Bitcoin.
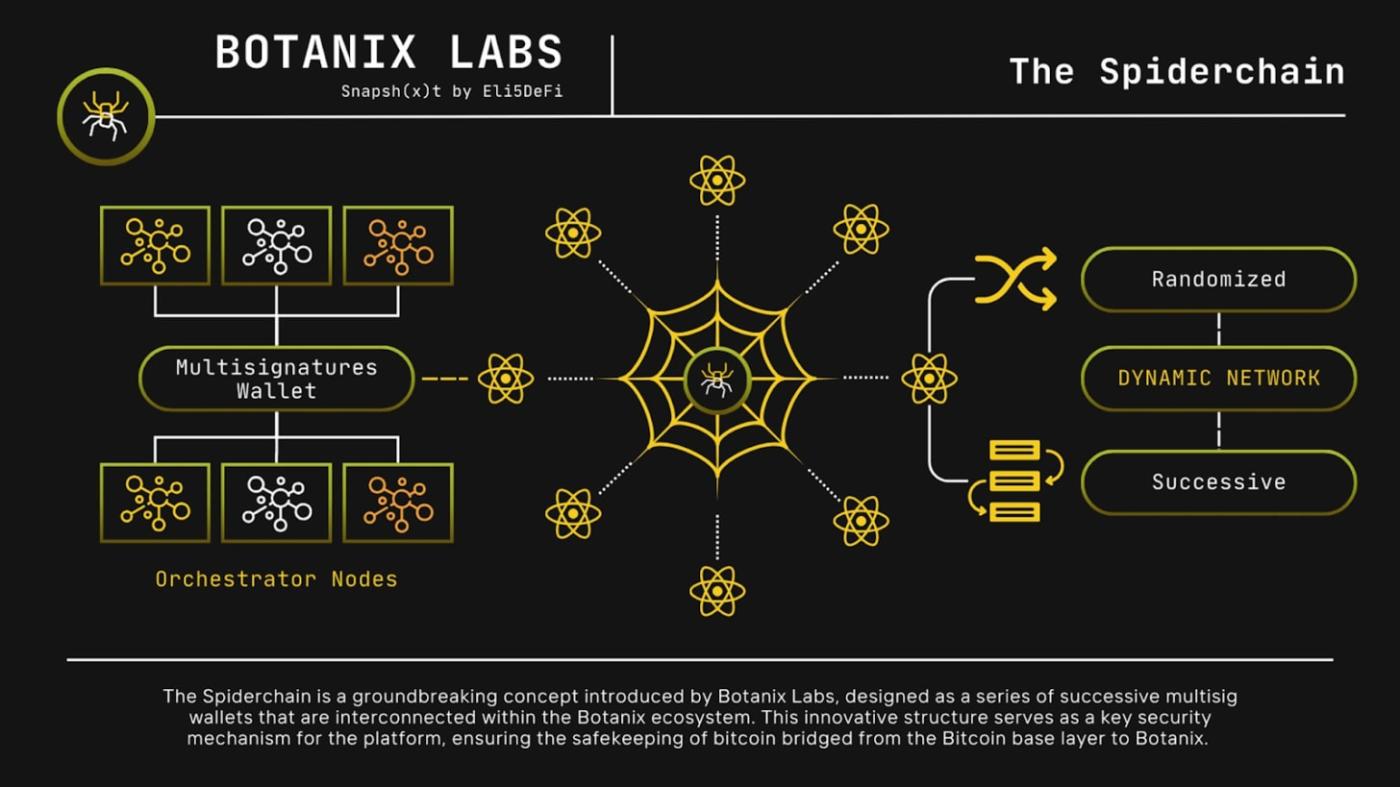
3.1. Botanix: Spiderchain and PoS Anchoring
Botanix is a new Bitcoin L2 that combines proof-of-stake validation and Bitcoin anchoring through a novel architecture called Spiderchain.
At the heart of Botanix is a rotating system of orchestrator nodes that manage the multisig Bitcoin bridge. These nodes are randomly selected using Bitcoin block hashes and require actual BTC to be staked on the Bitcoin L1 network. The network periodically records the state hash in Bitcoin, using Bitcoin as the final checkpoint for the Botanix chain.
This structure eliminates the need for a pre-determined operator and provides a permissionless exit path, allowing users to withdraw BTC at any time with certainty. On-chain activity is compatible with the EVM, and all gas fees are paid in BTC, not wrapped tokens or a separate gas asset.
Botanix also supports native DeFi applications, such as Rover, a Liquid staking protocol that distributes network fee revenue. Security relies on a PoS majority of honest orchestrators and fraud detection on Bitcoin's L1, striking a balance between performance and decentralization.
Through continuous updates and future development, Botanix is positioning itself as a reliable infrastructure layer for Bitcoin-native finance.
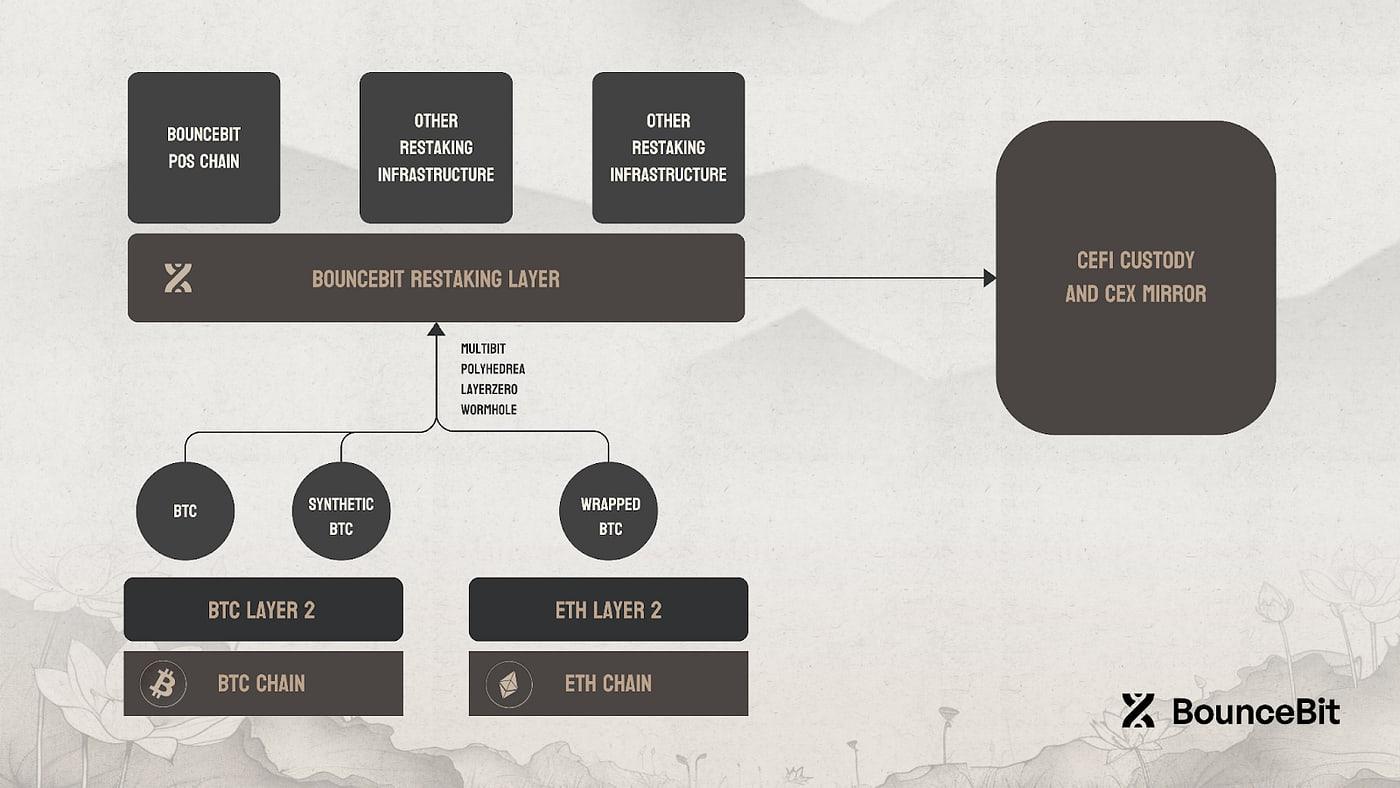
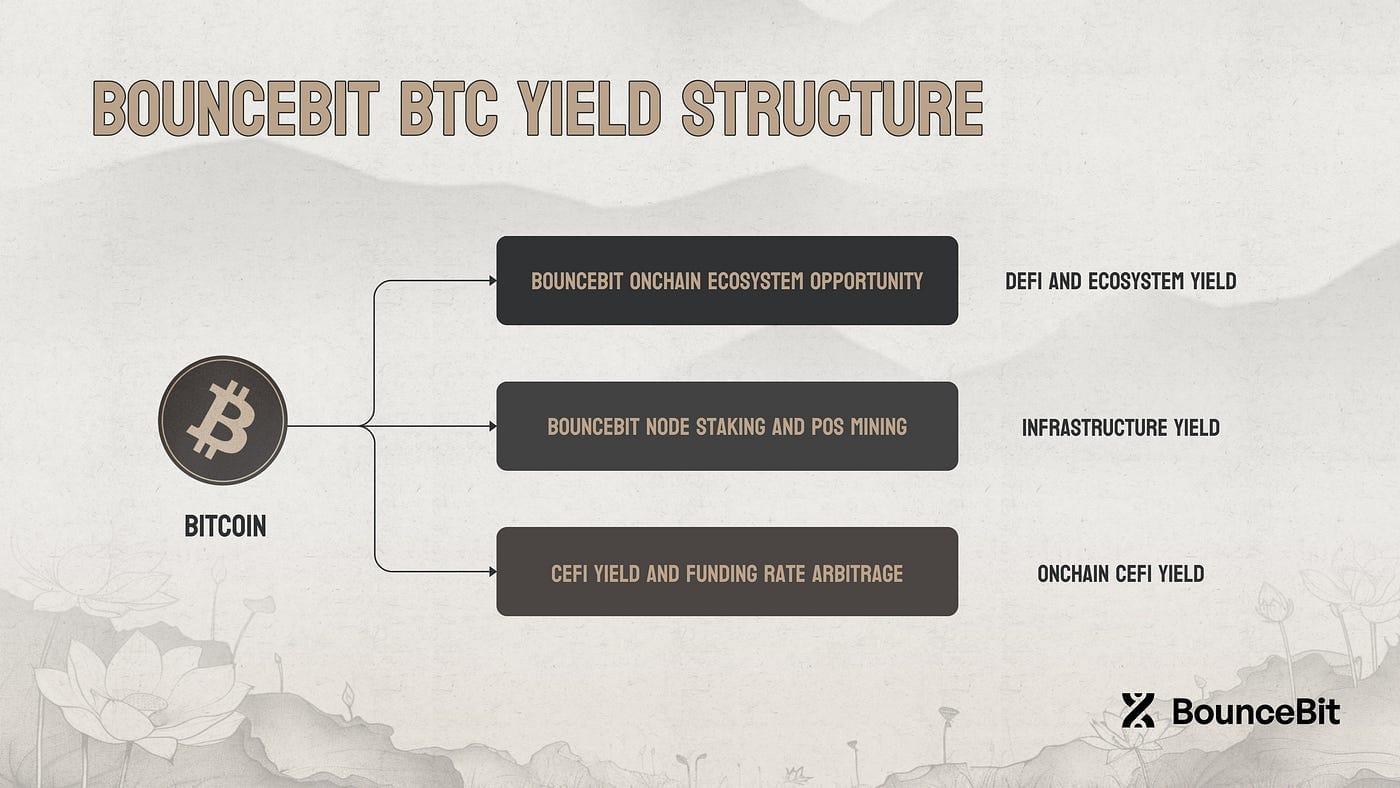
3.2. BounceBit: CeDeFi and Institutional Yield Layer
Bouncebit is an institutional service that combines CeFi infrastructure and DeFi accessibility to leverage Bitcoin as a foundation for core liquidity and trust.
4. Rollup-based protocol
Bitcoin creates a substantial technical barrier to this design.
Does not natively support complex verification logic or recursive proofs.
Real-time fraud detection is difficult due to the limited scripting language.
4.1. Merlin: zkEVM Rollup with BTC Staking
Merlin Chain is the most advanced attempt to create a zkEVM rollup on Bitcoin by combining zero-knowledge proofs, BitVM-based Bitcoin security, and a decentralized oracle network.
Off-chain transactions are aggregated and processed, a ZK proof of state change is generated, and this proof is then uploaded to Bitcoin L1 for finalization. To accommodate data storage not supported by Bitcoin itself, Merlin operates a Data Availability Committee (DAC), comprised of oracle nodes that store and verify off-chain data. Under the proposed structure, these DAC nodes are required to stake BTC and are penalized if they sign incorrect state updates that later become problematic.
Merlin provides a smooth EVM environment, supports assets like Ordinals and BRC-20, and uses MBTC (Merlin's Wrapped Bitcoin) as its base currency. It links BTC to Cobo via a multi-party computation (MPC) storage method at L1, and issues MBTC on the network.
This rollup model isn't completely trustless. Users must trust that at least one honest participant will raise concerns about fraudulent activity, and the bridge carries a storage risk. However, it offers high performance, Ethereum-level composability, and cryptographic guarantees of correctness.
Merlin has already garnered significant attention. With a peak TVL of over $3 billion, it demonstrates that for many users, practical DeFi returns are more important than theoretical perfection.
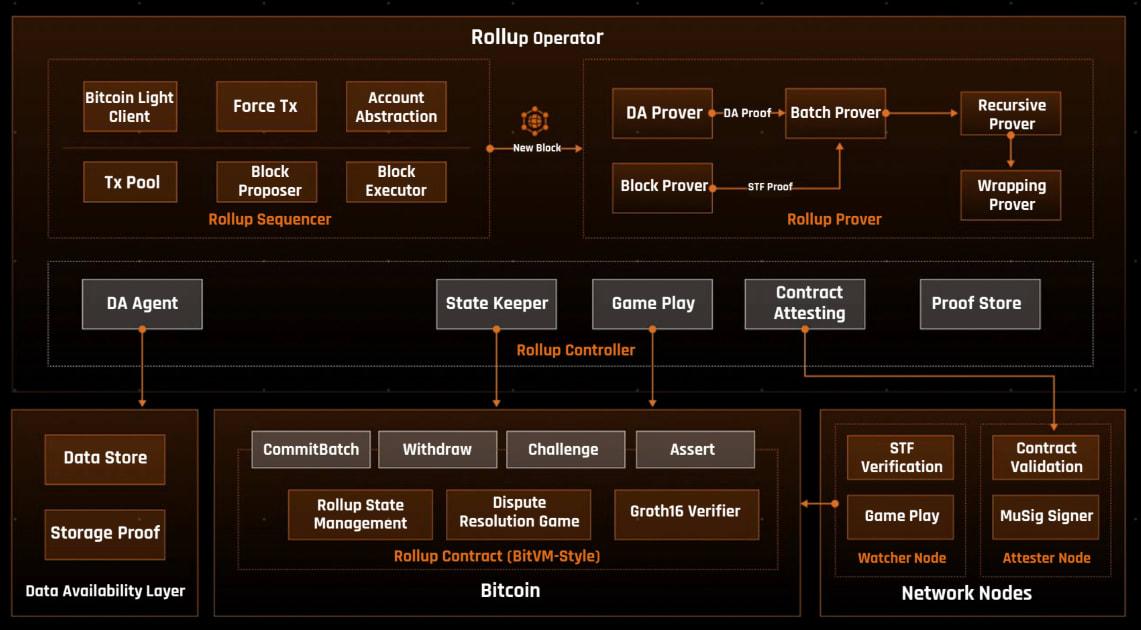
4.2. Bitlayer: BitVM + ZK Rollup Hybrid
BitLayer addresses the core gap between Bitcoin's unparalleled security and the scalability and programmability required by modern blockchains. By leveraging Bitcoin's base layer strengths, it inherits the same levels of trust, decentralization, and resilience that have made Bitcoin the world's most secure blockchain.
At the same time, Bitlayer introduced Turing-complete programming capabilities, enabling developers to create complex decentralized apps and smart contracts that were previously impossible with the Bitcoin framework.
Strategic partnerships with Sui, Base, Starknet, Arbitrum, Sonic SVM, Cardano, and Plume Network
YBTC.B, a Bitlayer wrapped BTC, is distributed to BSC, Sui, Avalanche, Ethereum, and Plume.
This growth has resulted in measurable results.
5. Hybrid consensus chain linked to Bitcoin
These chains don't upload data or settle transactions on Bitcoin. Instead, they work as follows:
5.1. Core: Satoshi Plus and BTC Hash Power Delegation
CoreDAO is a fully EVM-compatible Layer 1 blockchain, launched in 2023, that utilizes a unique hybrid consensus mechanism called Satoshi Plus. This model combines the following elements:
Delegated Proof of Work (DPoW): Bitcoin miners delegate hashing power to secure core blocks.
Delegated Proof of Stake (DPoS): CORE token holders stake to validators.
Non-custodial BTC staking: BTC holders support validators by locking their BTC in L1 without giving up custody rights.
In this model, Bitcoin miners contribute their hash power to the Core validator selection process and earn additional rewards without disrupting normal Bitcoin mining operations. BTC holders can participate in network consensus through time-locked transactions on Bitcoin's L1 network, enabling what Core calls "trustless Bitcoin staking."
Core offers fast block times, low fees, and full Ethereum compatibility. It offers DeFi, NFT, and dApp infrastructure that feels similar to Ethereum, but connects the validator set to Bitcoin's economic and mining power, creating a rarely attempted connection.
While Core has its own token (CORE) and governance process and does not directly anchor its state to Bitcoin, it complements rather than competes with Bitcoin. Rather than attempting to be Bitcoin's L2 in the narrowly technical sense, it aims to serve as a Bitcoin-linked smart contract chain where BTC users and miners benefit from on-chain activity.
With over 125 dApps already deployed and a growing user base, Core demonstrates a BTCFi strategy that blurs the lines between alternative L1 and Bitcoin infrastructure, offering an Ethereum-class ecosystem built on the trustworthiness and capital base of Bitcoin.
6. Lightning Network: Parallel Tracks
No discussion of Bitcoin's scaling architecture would be complete without the Lightning Network, a layer-2 solution specifically designed for fast, low-cost payments. Unlike the BTCFi protocol, which focuses on lending, yield generation, and tokenization, Lightning operates on a separate track and excels at its original goal: enabling Bitcoin to function as peer-to-peer cash.
Lightning works by creating state channels between users. By locking BTC in a channel, two parties can transact off-chain with virtually no delay and negligible fees. Only the net result is settled on the Bitcoin underlying layer. This model dramatically increases transaction throughput (Lightning can theoretically handle millions of transactions per second) and reduces transaction costs to mere cents.
As of 2025, the Lightning Network secures $400-500 million in BTC liquidity and powers real-world payment apps like Strike, particularly in emerging markets where fast transfers and low fees are crucial.
However, while Lightning excels at payments, it's not ideal for DeFi. Its smart contract capabilities are minimal, optimized for simple channel scripts rather than complex financial logic. While you can buy coffee or stream micropayments, you can't launch a lending protocol or deploy a decentralized exchange using Lightning. Liquidity is also fragmented across thousands of channels, making it difficult to aggregate capital for pooled DeFi strategies.
While Lightning remains specialized and DeFi integration is minimal, its strategic importance is clear. It complements the BTCFi protocol by allowing BTC to be moved cheaply and instantly. The BTCFi platform unlocks value by locking BTC in yield strategies. As bridging technology improves, Lightning liquidity will increasingly flow into BTCFi flows, connecting Bitcoin's spending side with the productive capital layer.
7. Development of new ideas and infrastructure
As we explored in Part 2, infrastructure layers are freeing up Bitcoin's idle capital by moving complexity off-chain and re-anchoring trust to L1.
New entrants are already pushing this idea further. Plasma, an emerging Bitcoin-anchored sidechain designed for fee-free, stablecoin-friendly settlement, combines EVM compatibility with privacy features. Arch Network pioneered a bridgeless execution layer directly on Bitcoin, enabling high-throughput dApps without the need for wrapped assets. While their designs differ, both reflect the same ethos: innovating around Bitcoin's strengths without sacrificing them.
The path forward for BTCFi will be modular and diverse. However, infrastructure is only one side of the equation. In Part 3, we'll move to the asset and custody layers, focusing on how Bitcoin is moved, stored, and represented across these networks.
Be the first to discover insights from the Asian Web3 market, read by over 13,000 Web3 market leaders.
🐯 More from Tiger Research
이번 리서치와 관련된 더 많은 자료를 읽어보세요.Disclaimer
This report has been prepared based on reliable sources. However, we make no express or implied warranties as to the accuracy, completeness, or suitability of the information. We are not responsible for any losses resulting from the use of this report or its contents. The conclusions, recommendations, projections, estimates, forecasts, objectives, opinions, and views contained in this report are based on information current at the time of preparation and are subject to change without notice. They may also differ from or be inconsistent with the opinions of other individuals or organizations. This report has been prepared for informational purposes only and should not be construed as legal, business, investment, or tax advice. Furthermore, any reference to securities or digital assets is for illustrative purposes only and does not constitute investment advice or an offer to provide investment advisory services. This material is not intended for investors or potential investors.
Tiger Search Report Usage Guide
Tigersearch supports fair use in its reports. This principle allows for the broad use of content for public interest purposes, provided it does not affect commercial value. Under fair use rules, reports may be used without prior permission. However, when citing Tigersearch reports, 1) "Tigersearch" must be clearly cited as the source, and 2) the Tigersearch logo must be included. Reproducing and publishing materials requires separate agreement. Unauthorized use may result in legal action.