This report was conducted by Tiger Research, analyzing the permissionless cross-chain protocol of Hyperlane, which has now connected over 150 blockchains with a modular security framework and breakthrough potential in eliminating integration barriers in Web3 interoperability.
TL;DR
Truly permissionless deployment: Unlike competitors requiring approval processes or whitelisting, Hyperlane allows any developer to immediately deploy and connect to multiple chains without gatekeeping, creating a completely different onboarding model compared to other interoperability protocols.
Flexible modular security: While other bridges use fixed security models, Hyperlane's Interchain Security Module (ISM) allows applications to self-configure security levels (from basic validator signatures to multi-layered verification), enabling infrastructure that can support both high-speed microtransactions and transactions of assets requiring maximum security.
Developer-first architecture: Hyperlane's TypeScript SDK, CLI tools, and comprehensive documentation help lower technical barriers in cross-chain integration. Instead of complex self-deployment, developers only need to call simple APIs to access interchain messaging.
1. A Turning Point for Blockchain Connectivity
The blockchain ecosystem is shifting from an isolated development model to genuine connectivity. Instead of building closed environments, more and more projects are seeking integration into a larger network.
[The rest of the translation follows the same professional and accurate approach, maintaining the technical terminology and style of the original text.]Hyperlane Warp Routes play a crucial role in expanding Hyperlane's vision of modular, permissionless interoperability between chains. Developers only need to configure contracts according to the specifics of each chain, while the rest — from messaging, verification to distribution — are handled by Hyperlane's infrastructure, helping them deploy cross-environment connections without having to build complex translation mechanisms.
2.3. Modular Security: Interchain Security Module (ISM)
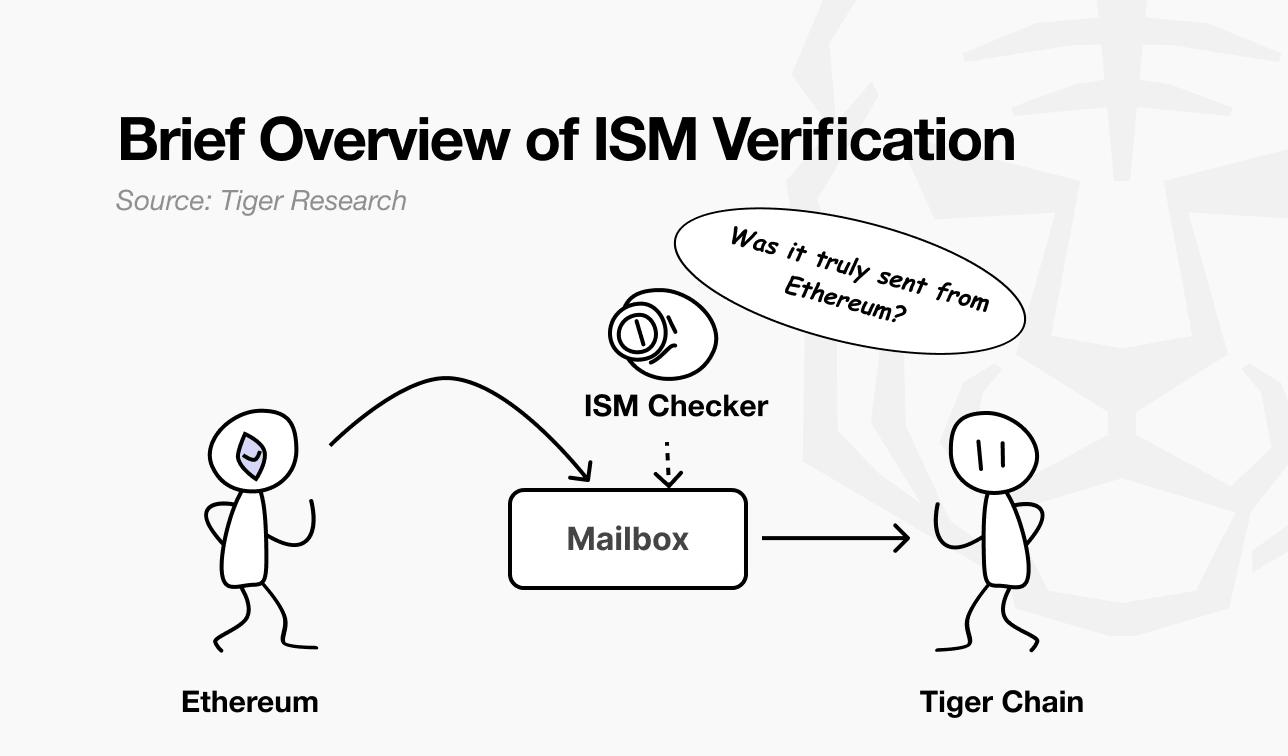
While Hyperlane allows seamless message and asset transfer between different chains — a key strength in scalability — it also poses an important challenge: How can the receiving chain be certain that a message truly comes from the declared source chain? Sending a message is one thing, but verifying its authenticity is another.
To solve this issue, Hyperlane introduces the Interchain Security Module (ISM) — a modular security system that helps verify the authenticity of messages before the destination chain accepts them. ISM is an on-chain smart contract used to verify whether a message was actually created from the source chain, thereby ensuring anti-forgery and source authenticity.
Simply put: when the Mailbox of the destination chain receives a message, it asks: "Does this message truly come from the original chain?". Only when verification is successful, the message is forwarded to its destination. If verification fails or there are suspicious signs, the message will be rejected.
This process is similar to border control when you travel internationally. Before entry, immigration officers check the validity of your passport: "Was this passport truly issued by your country?" The passport contains anti-forgery elements and cryptological components proving its legitimacy. While anyone can create fake documents, only passports that can prove their origin through cryptographic verification are accepted.
Importantly, ISM has high flexibility, allowing configuration of security models that suit service needs. In practice, security requirements vary by context. For example, a small-value token transaction might only need basic validator signatures for quick processing. Conversely, a multi-million dollar asset transaction might require multi-layered security models — including Hyperlane validators, external bridges like Wormhole, along with additional multisig verification.
In this way, the ISM framework reflects an important design decision: Hyperlane prioritizes both connectivity and security through modular verification. Applications can customize their own security models while maintaining the protocol's permissionless nature.
3. Developer Tools and Accessibility: The Easiest Connection Method
Hyperlane prioritizes developer experience by providing high accessibility and ease of use. The toolset including command-line interface (CLI) and TypeScript-based SDK are core components that help integrate new chains into the Hyperlane ecosystem, send interchain messages, and configure Hyperlane Warp Routes.
Both CLI and SDK are completely open-source and anyone can use them. Developers only need to install code from GitHub to start integration, without needing licenses or approval processes. Official documentation provides step-by-step guidance, making it easy for even blockchain developers with little experience to access.
4. Hyperlane's Future Path
Hyperlane has demonstrated rapid growth since launching its testnet in the second half of 2022. Initially named Abacus, the project rebranded to Hyperlane in autumn 2022 and began implementing its ecosystem expansion strategy.
The year 2023 marked the foundational stage for Hyperlane's technical development. The team introduced a modular security stack, allowing customized security configuration for each chain. In parallel, Hyperlane implemented a permissionless deployment system, enabling any developer to connect new chains without permission.
Simultaneously, the project focused on enhancing developer experience, simplifying the complex cross-chain process, and making multi-chain application development more intuitive. Through integration with key projects like Circle, Hyperlane also achieved significant progress in ecosystem expansion.
4.1. Positioning for Breakthrough Growth
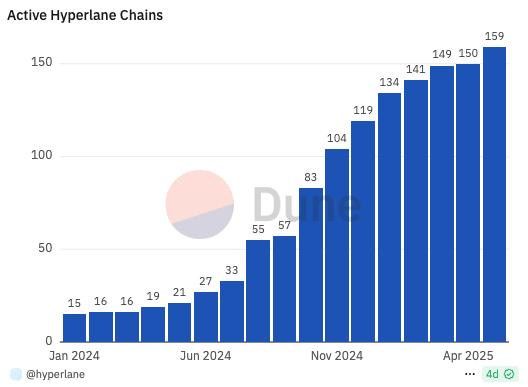
Currently, Hyperlane supports over 150 blockchains, including Ethereum, Solana, and Avalanche. With bridge asset volumes reaching billions of dollars, the protocol has moved beyond the testing phase to commercial-scale deployment.
One of the most notable trends is network effect. The more chains connect to Hyperlane, the stronger the momentum for other chains to join. New participants can immediately access liquidity, users, and interoperability from connected networks. Developers prioritize infrastructure supporting broad compatibility, while users seek more utilities and flexibility.
Two core competitive advantages are driving Hyperlane's growth:
Superior connectivity with over 150 chains — far ahead of competitors.
A permissionless architecture that significantly reduces onboarding barriers and accelerates ecosystem expansion.
Combined, these advantages provide Hyperlane with a growth trajectory superior to traditional interoperability solutions.
4.2. Making $HYPER Useful
After launching the $HYPER token in April 2025, Hyperlane's greatest challenge is ensuring long-term utility for the token. The critical question is: Can $HYPER evolve from a speculative asset to an indispensable part of the protocol's operation?
[The translation continues in the same manner for the rest of the text, maintaining the specified translation rules for specific terms.]Strengthening security remains a top priority. Through the bug bounty program, Hyperlane awards up to $2.5 million to those who discover critical vulnerabilities in smart contracts. This has proven to be an effective mechanism to encourage active participation from security researchers.
However, risks still exist — especially due to the open-source and permissionless nature of the protocol. Continuous monitoring is necessary, particularly when users customize modules, which could potentially create unforeseen vulnerabilities.
4.4. Becoming the Core Infrastructure for the Interactive Web3 Era
As interoperability becomes a fundamental requirement of Web3, Hyperlane's progress and potential become increasingly important. If the project's vision is realized, users can interact with blockchain services without worrying about which chain they are using.
This represents a blueprint for a truly unified blockchain ecosystem. At this critical moment, Hyperlane's next steps will be decisive in realizing that vision to what extent.
Explore the Web3 market in Asia with Tiger Research. Join a community of over 13,000 pioneers to receive exclusive market analyses!
🐯 More from Tiger Research
Read more reports related to this research.The Open Gaming Manifesto: How B3 Will Save the Web3 Gaming Industry
Chromia's Vector Database: A Pioneering Convergence of AI and Blockchain
Disclaimer
This report is partially sponsored by Hyperlane. However, we do not guarantee explicit or implied accuracy, completeness, or suitability of the information. We disclaim any liability for any losses arising from the use of this report or its content. The conclusions and recommendations in the report are based on available information at the time of drafting and may change without prior notice. All projects, estimates, forecasts, goals, views, and opinions mentioned in this report may change without notice and may differ from or be contrary to the views of others or other organizations.
This document is for informational purposes only and should not be considered legal, business, investment, or tax advice. Any references to securities or digital assets are for illustrative purposes only and do not constitute investment recommendations or offers of investment advisory services. This document is not intended for investors or potential investment targets.
Terms of Use
Tiger Research allows reasonable use of its reports. "Fair use" is a principle that permits using part of the content for public benefit, provided it does not harm the commercial value of the document. If the use complies with fair use purposes, reports may be used without prior permission. However, when citing Tiger Research reports, the following requirements must be followed: 1) Clearly cite the source as "Tiger Research" 2) Attach the Tiger Research logo (black/white). If the document is edited and republished, a separate agreement is required. Unauthorized use of reports may lead to legal action.