Written by: Yangz, Techub News
Monero, an old-school privacy coin that has gradually been labeled as "marginalized" in the industry's trend towards mainstream and compliance, attracted attention yesterday due to a "peaceful occupation" by an unknown entity. However, this spotlight seemed more like a "humiliation". Yesterday evening, a Layer1 Qubic account, led by IOTA's former co-founder Sergey Ivancheglo (alias Come-From-Beyond), forwarded media tweets stating that the "Monero (XMR) experiment is proceeding smoothly as planned, and everything will be revealed at the right time." The so-called experiment referred to a 51% "attack" on Monero, successfully raising concerns about one of the most destructive network threats in cryptocurrency. After the news broke, XMR's price immediately dropped, falling by 4.5% within an hour.
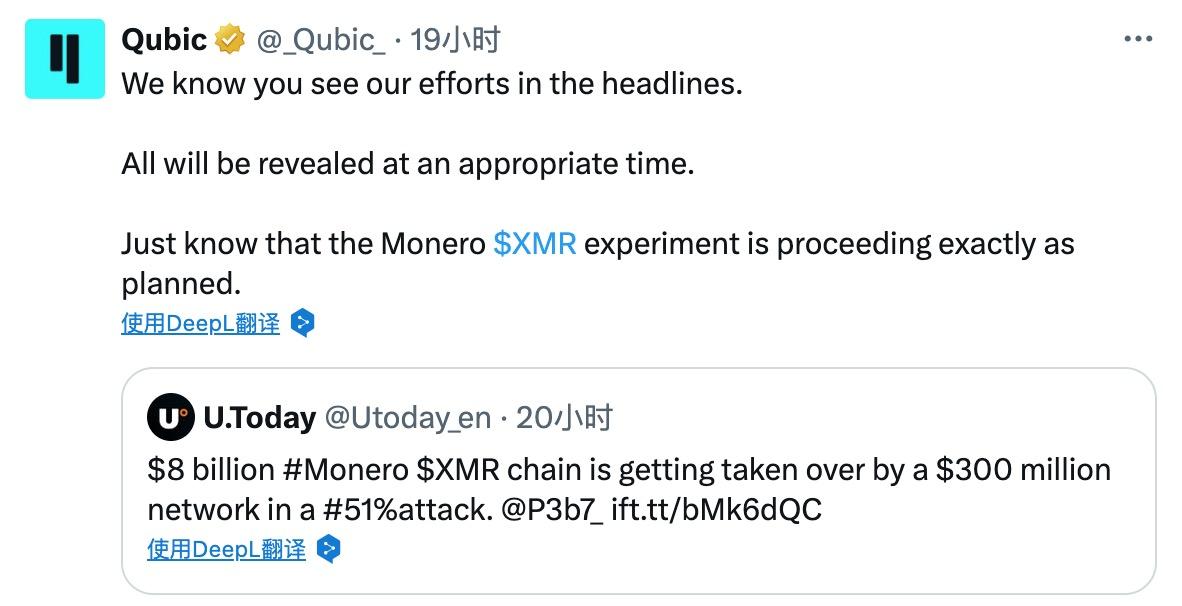
Three hours later, Qubic again posted, officially announcing the successful control of 51% of Monero's network hashrate. Surprisingly, this month-long "occupation" was not intended to cause damage: Qubic neither initiated a double spend attack nor implemented a destructive hard fork. Instead, it was more like a carefully designed proof that in a decentralized world, code's robustness cannot withstand human profit-seeking, and miners will voluntarily "switch sides" if provided with sufficiently attractive economic incentives.
Qubic: An "Unknown" Born for AI
According to Qubic's introduction, its original intention was not to become another high-speed public chain or financial infrastructure, but to carry a fully on-chain decentralized AI model called AIGarth. To achieve this goal, Qubic adopted a lightweight design, allowing verification nodes to run in RAM. It uses a Quorum consensus mechanism and employs "Useful Proof of Work" (uPoW) to use computing power for actual computational tasks rather than meaningless hash collisions.
Moreover, Qubic's core innovation lies in "Outsourced Computations". Simply put, Qubic's miners can not only maintain network security but also "rent out" computing power to external tasks (such as training AI or providing computing power for other chains), thereby obtaining higher returns. However, theory needs practical verification, and to demonstrate its uPoW and outsourced computing capabilities, Qubic chose Monero, known for its privacy and ASIC resistance, as the experimental subject.
Experiment: "Peacefully Occupying" Monero through Economic Incentives
Qubic's "Monero Mining Plan" can be roughly divided into two stages: In the first stage of exploratory layout, Qubic allocated computing power to two parts. One part continued training AIGarth, while the other was used for mining Monero. Due to uPoW's high efficiency, mining returns once reached 3 times that of pure Monero mining, attracting numerous miners to join the Qubic network. Subsequently, the Qubic community voted to make a critical adjustment to the revenue distribution mechanism, changing from 100% token buyback and burn to a new model of 50% token destruction and 50% direct rewards to verifiers. This adjustment visibly enhanced miner returns, further drawing away Monero's original mining pool hashrate.
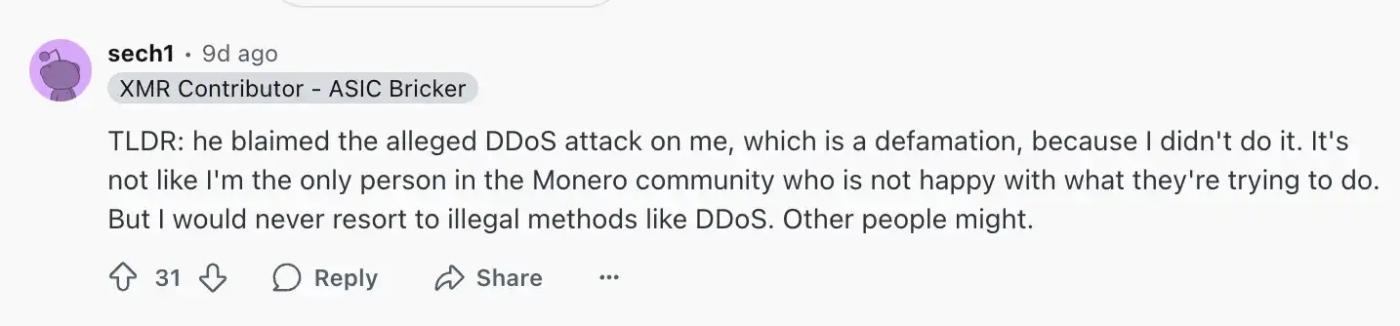
Of course, this "occupation" was not smooth sailing. According to Qubic's description, when it first attempted to occupy 51% hashrate advantage on August 2nd, it encountered resistance from the Monero community. Some of Qubic's verification nodes reported suffering DDoS attacks, which Qubic summarized as lasting a week. Ivancheglo pointed the finger at Sergei Chernykh (nickname sech1), the main developer of Monero mining software XMRig, suggesting possible involvement, but sech1 immediately issued a statement on Reddit explicitly denying any connection to the incident.
Despite encountering resistance, Qubic's experiment continued to advance. On August 11th, Qubic deployed a more complex "Selfish Mining" strategy by selectively delaying block broadcasting, artificially creating isolated blocks, and releasing the privately stored longest chain at critical moments, ultimately successfully testing the network reorganization of Monero. Data provided by Qubic's chief developer dkat showed that in a critical 122-block test window, Qubic mined 63 blocks, accounting for 51.6%, exceeding the predetermined goal.
Surprisingly, upon completing the takeover test, the Qubic team explicitly stated that they would not actually take over Monero's consensus mechanism. This decision considered Monero's price stability, but the deeper reason was that this action was a verification experiment from start to finish. The Qubic team stated they hope to ultimately achieve a win-win: Qubic miners would provide security protection for Monero while rewards would be distributed through Qubic's mining pool.
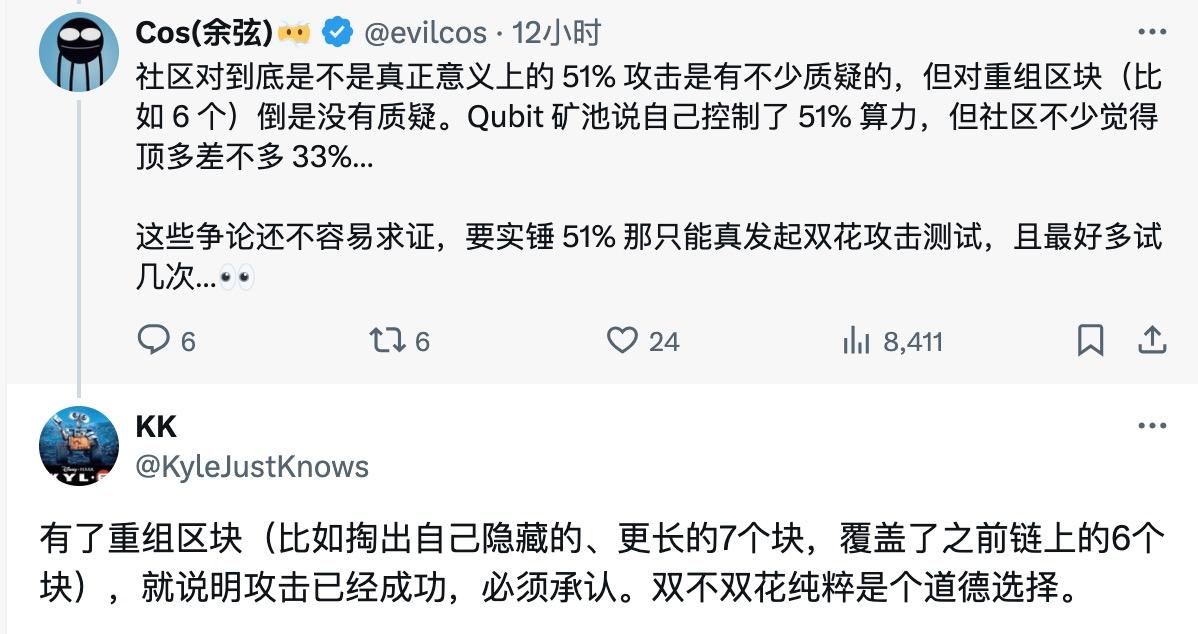
It's worth noting that although Qubic claims to currently control 51% of Monero's network hashrate, the community remains skeptical. Slow Fog founder Yu Xin pointed out that the community generally believes Qubic controls only around 33% of Monero's network hashrate. Some argue that "with block reorganization, the attack has succeeded and must be acknowledged. Whether it's a double spend is purely a moral choice."
Summary
Although the dispute about hashrate proportion remains unresolved, in this "bloodless occupation", Qubic, with a market value of just $300 million, successfully pushed the privacy coin giant, 20 times its size, into crisis. It declared to the industry that economic incentives are often more decisive than technological beliefs.
Moreover, the more thought-provoking aspect of this experiment was its "non-aggressive" nature. Qubic did not act maliciously, but calmly proved a fact: in the decentralized world, value creation is more powerful than forced control. This resembles classic disruptive business cases. Kodak was not defeated by better film, but by digital technology; taxis were not disrupted by cheaper taxis, but by Uber.
As Dan Dadybayo, researcher and strategist at Unstoppable Wallet, pointed out, "This is not just a Monero story. This is a warning to all PoW networks. Having strong mathematical capabilities is not enough. We need resilient infrastructure with aligned incentive mechanisms. Otherwise, the next 'attack' will look nothing like an attack, just a better transaction."