Hackers linked to North Korea are intensifying their attacks on the cryptocurrency sector, and a recent investigation has revealed the evolved methods of the Lazarus Group.
On-chain analyst ZachXBT has uncovered a series of incidents related to the regime's cyber operations, including fake developer profiles and complex money laundering strategies.
Lazarus Hackers Steal Millions of Dollars…North Korea Intensifies Crypto Attacks
On June 29, on-chain detective ZachXBT revealed that the Lazarus Group scammed $3.2 million in digital assets from a user on May 16.
The stolen funds were quickly converted from Solana to ETH. The hackers subsequently deposited 800 ETH into Tornado Cash, a privacy protocol for hiding cryptocurrency transactions.
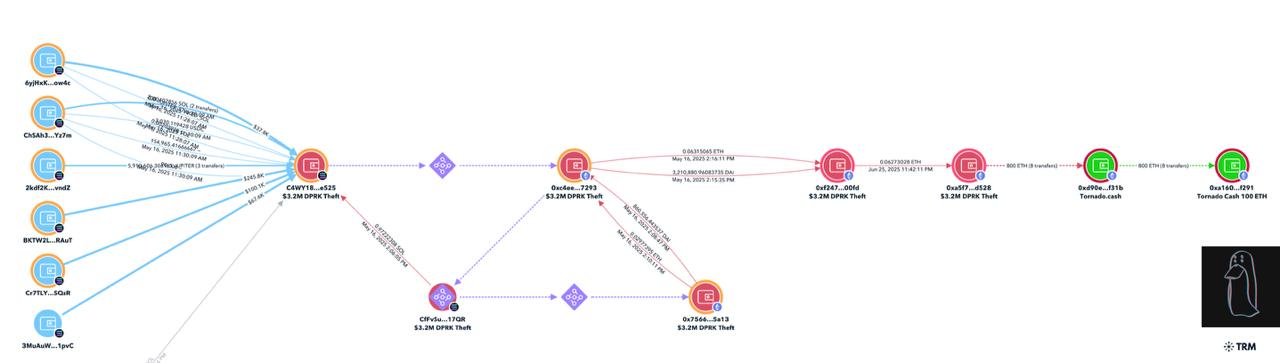
At the time of the report, approximately $1.25 million remained in an ETH wallet holding Dai and ETH.
Meanwhile, this attack is part of a series of activities by the Lazarus Group, who are increasingly targeting high-value crypto assets.
On June 27, ZachXBT stated that the group was connected to a major attack that impacted several Non-Fungible Token projects related to Pepe's creator Matt Furie. The attack also affected projects like ChainSaw and Favrr.
1/ Multiple projects tied to Pepe creator Matt Furie & ChainSaw as well as another project Favrr were exploited in the past week which resulted in ~$1M stolen
— ZachXBT (@zachxbt) June 27, 2025
My analysis links both attacks to the same cluster of DPRK IT workers who were likely accidentally hired as developers. pic.twitter.com/85JRm5kLQO
The hacking attack began on the 18th, with multiple hackers taking control of Non-Fungible Token contracts, issuing and dumping Non-Fungible Tokens, causing approximately $1 million in damage to these projects.
ZachXBT's investigation revealed that the hackers moved the stolen funds to three wallets. Eventually, they converted some ETH to stablecoins and transferred them to the centralized exchange MEXC.
Meanwhile, stablecoin transfer patterns connected to specific MEXC deposit addresses suggest that the attackers were involved in multiple crypto projects.
Additionally, the analysis uncovered connections to GitHub accounts with Korean language settings and time zones matching North Korean activities.
"Other indicators revealed in internal logs point to irregularities in the resume of suspected North Korean IT workers. Why would a developer claiming to reside in the US have Korean language settings, use Astral VPN, and have Asian/Russian time zones?" ZachXBT questioned.
In the case of Favrr, investigators suspect that the project's Chief Technology Officer, Alex Hong, might be a North Korean IT worker. ZachXBT also reported that Hong's LinkedIn profile was recently deleted and his career record could not be verified.
In reality, these incidents highlight North Korea's continued role in cryptocurrency theft. Blockchain analysis company TRM Labs recently linked North Korean hackers to stealing approximately $1.6 billion, which represents about 70% of all stolen crypto assets this year.





