The $90 million hacking incident of Iran's largest cryptocurrency exchange Nobitex has drawn global attention. However, newly revealed blockchain data has exposed an even larger issue.
According to the forensic report by blockchain information company Global Ledger, Nobitex had been systematically moving user funds using money laundering techniques several months before the June 18 attack.
Iran's Nobitex, Money Laundering User Funds Before Hacking?
According to on-chain data, Nobitex used a method called pill chaining. This involves dividing large amounts of Bitcoin into small pieces and moving them through short-term wallets.
This technique makes fund tracking difficult and is often used to hide the source of funds. In Nobitex's case, analysts discovered a pattern of BTC circulating in consistent 30-coin units.
Global Ledger also found that Nobitex used temporary deposit and withdrawal addresses, a behavior known as chip-off trading. These disposable addresses channel BTC into new wallets, obscuring liquidity paths.

'Rescue Wallet' Not New
After the hacking, Nobitex claimed to have moved remaining funds as a safety measure. On-chain activity showed 1,801 BTC (worth approximately $187.5 million) moved to a newly created wallet.
However, this wallet was not new. Blockchain data tracks usage records dating back to October 2024. This wallet had been collecting chip-off funds for a long time.
This "rescue wallet" had already received multiple 20-30 BTC transfers following the same money laundering pattern before the hack occurred.
Post-Hack Activity, Continued Control
Hours after the hack, Nobitex moved funds from the exposed hot wallet to other internal addresses. This complete balance transfer indicated that Nobitex maintained operational control.
On June 19, investigators observed 1,783 BTC being transferred to a new destination wallet. This aligned with Nobitex's asset protection claims, but now with additional context.
This flow suggests that Nobitex was following its existing money laundering plan rather than responding to the hack.
The pro-Israel hacking group Gonjeshke Darande released files exposing Nobitex's internal wallet structure.
While the hack shocked users, blockchain data shows that Nobitex had been moving funds this way for months.
Old wallets connected to the exchange regularly transferred Bitcoin to new wallets. There, funds were divided into smaller amounts and moved again. Often transferred in 20 or 30 BTC units.
This method makes it difficult to track where funds are going. It's similar to how some people hide traces when moving funds through cryptocurrency.
Importantly, this wasn't something Nobitex started after the hack. They had been doing this long before and continued afterward. As if it were a standard procedure.
One wallet—bc1q…rrzq—appears repeatedly. This wallet received many user deposits and seems to be the starting point for these hard-to-trace fund movements.
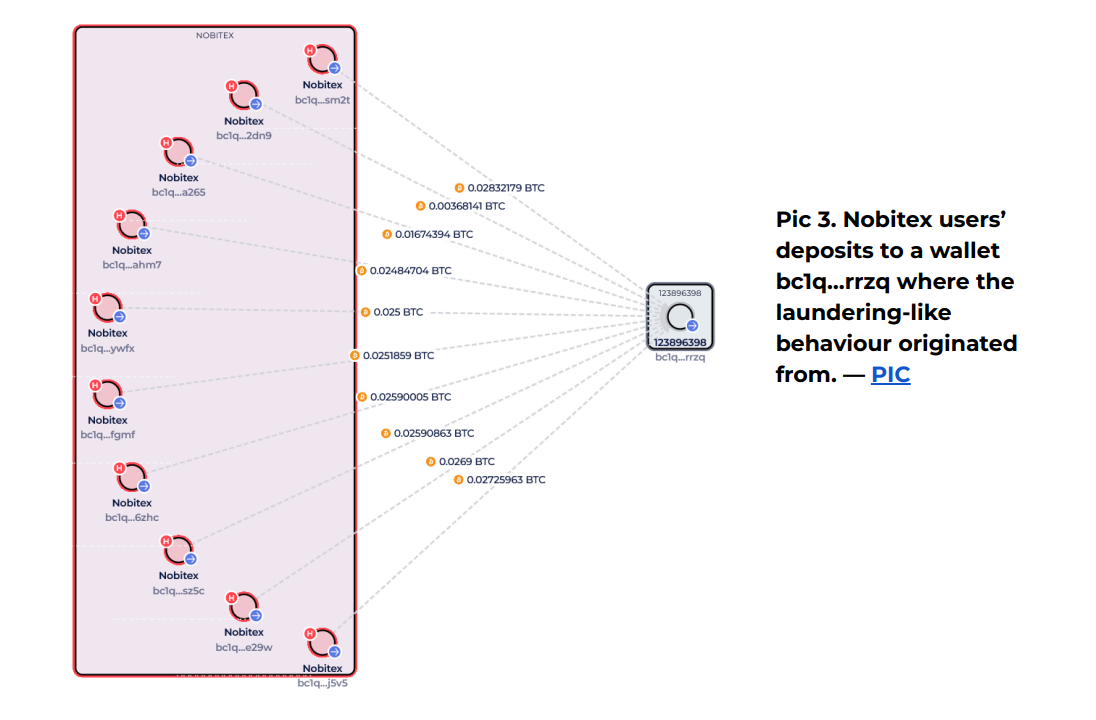
In summary, the hack did not change how Nobitex handles funds. It merely exposed ongoing covert activities to the public.







